Cardiac remote patient monitoring (RPM) offers valuable diagnostic and therapeutic benefits, yet it also comes with significant cybersecurity risks. Protecting patient data and ensuring device security against emerging threats is vital for cardiology and electrophysiology practices.
This article dives into essential vulnerability assessment tools and strategies to strengthen your RPM program, reduce risks, and stay compliant in today's connected healthcare environment.
Healthcare organizations face a growing number of cyber threats, making strong vulnerability assessment protocols critical for cardiac RPM systems. As RPM adoption increases, these systems become prime targets for cybercriminals. Potential risks include unauthorized access to patient data, data interception during transmission, and issues from outdated or unpatched software.
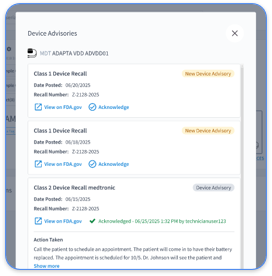
Recent events underline the seriousness of these dangers. Certain patient monitors have vulnerabilities that could allow remote control or device denial by unauthorized users. Additionally, a hard-coded backdoor in Contec CMS8000 monitors was found to enable undetected data transmission to third parties, risking remote code execution and data theft.
The financial and regulatory fallout can be substantial. Not securing RPM data may lead to HIPAA breaches, triggering legal penalties, regulatory oversight, and patient lawsuits. Beyond costs, such incidents can harm a practice’s reputation and weaken patient trust, which are hard to rebuild.
A forward-thinking vulnerability management plan brings clear advantages. It safeguards patient safety by protecting critical cardiac data, shows a commitment to security, minimizes disruptions from cyber incidents, and builds patient confidence in data protection. This approach also supports sustainable growth, allowing practices to scale RPM programs without increasing security risks.
Vulnerability assessment tools play a key role in spotting and addressing security gaps, but starting with a secure, compliant platform is just as important.
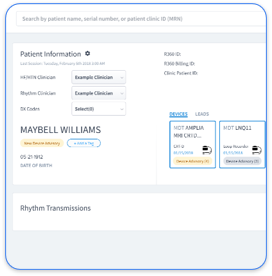
Rhythm360, provided by RhythmScience, is a cloud-based, vendor-neutral, HIPAA-compliant solution tailored for managing patients with Cardiac Implantable Electronic Devices (CIEDs) and chronic conditions like Heart Failure (HF) and Hypertension (HTN).
Key benefits of Rhythm360 include:
Schedule a demo to explore how Rhythm360 can enhance your cardiac RPM program with security and efficiency.
Network scanners are your first step in spotting vulnerabilities in cardiac RPM setups. They identify all connected devices, from monitoring equipment to data terminals, by cataloging open ports, services, and potential entry points. This creates a detailed view of your system’s exposure to threats.
Using Rhythm360 can simplify this process. Its centralized data platform reduces the number of endpoints to scan, helping your security team focus on critical areas and avoid oversight.
Device configuration audit tools evaluate the security of individual medical devices in your RPM network. They check for default passwords, unnecessary services, outdated firmware, and improper setups that could be exploited. Recent alerts emphasize their importance. Some patient monitors have hidden functions that bypass security controls, risking device manipulation. This shows the need for ongoing configuration checks.
Rhythm360 aids this process with a unified dashboard, showing device connectivity across manufacturers and highlighting issues for deeper review.
DLP solutions guard against unauthorized sharing of patient data, whether accidental or deliberate. In cardiac RPM, they monitor data across networks and cloud services to keep sensitive information within secure boundaries.
Start with data classification, tagging cardiac data like device readings and diagnostic reports by sensitivity. Focus on patterns specific to cardiac data, like device IDs and clinical codes.
Network-based DLP is crucial for detecting data theft from monitoring devices. Recent findings show some monitors may leak patient data when online.
Rhythm360 helps by logging all communications securely within its platform for compliance tracking.
Each tool type plays a distinct role in a well-rounded security plan. For example, network scanners give broad oversight but might miss app-specific issues, while device audits secure individual components. Penetration testing checks how all defenses work together.
High-risk setups or those with recent incidents may need more frequent checks. Major changes, like adding devices or updating software, should prompt immediate assessments. Focus resources on critical systems and data for the best impact.
Schedule a demo to see how Rhythm360 complements your vulnerability assessment efforts with integrated features.
Implementing a solid vulnerability assessment program for cardiac RPM takes thoughtful planning and gradual steps. Start with a baseline review to gauge your current security status and pinpoint urgent issues.
Focus on high-risk vulnerabilities first, building processes for regular assessments. Begin with network scanning to map your setup, then conduct device audits for basic security. Next, add web application scans and schedule penetration tests.
Train staff to interpret results, prioritize fixes, and escalate critical issues. Develop clear response procedures, especially for risks to patient safety or data.
If internal expertise is limited, consider managed security services for tasks like penetration testing. Many practices benefit from combining in-house efforts for routine tasks with external help for specialized needs.
Vulnerability assessments for cardiac RPM must align with regulations like HIPAA, FDA device rules, and new cybersecurity guidelines. HIPAA’s Security Rule mandates regular evaluations of systems handling protected health information, covering access, audits, and data transmission.
FDA guidelines stress ongoing vulnerability management for medical devices. While manufacturers monitor threats, healthcare providers must adapt safeguards to their environments. Document all assessment activities, including schedules, findings, and fixes, to prove compliance during audits.
Platforms like Rhythm360 can assist with centralized record-keeping.
Schedule assessments based on system importance and patient needs. Run network and web app scans monthly, or more often for high-risk setups. Audit device configurations quarterly or after new deployments. Conduct penetration testing yearly or twice yearly, with extra tests after major changes or incidents.
Rhythm360 offers a strong base with centralized data management and HIPAA compliance, but it’s only part of a full security plan. Vulnerability tools address risks beyond the platform, including network, other devices, and human factors. Combine it with a broader strategy for complete protection.
Without assessments, your practice could face severe security breaches, risking patient safety and data exposure. Attackers might access or alter data, disrupt monitoring, or cause major HIPAA violations. Penalties, lawsuits, reputational harm, and care disruptions are real possibilities, as recent monitor vulnerabilities prove.
Plan assessments to avoid impacting care, running tools during off-hours or maintenance windows. Network scans often operate unnoticed in the background, while intensive tasks like penetration testing should align with planned downtime. Communicate with clinical staff about schedules and how to report odd system behavior.
Choose tools suited for medical devices and healthcare workflows. Prioritize those detecting device-specific issues, integrating with EHRs, offering clear compliance reports, reducing false alerts, and providing fix guidance without disrupting care. Ensure vendors know healthcare regulations and offer customization for your device mix.
With cyber threats targeting healthcare on the rise, vulnerability assessments are essential for cardiac RPM programs. The dangers of weak security, from regulatory fines to patient safety risks, far outweigh the effort needed for proactive measures.
A strong strategy combines network scanning, web testing, device audits, penetration testing, threat intelligence, staff training, and data protection. Each element tackles specific risks, building a security foundation that safeguards data and ensures compliance.
Pair these tools with a reliable platform for the best results. Rhythm360 provides a vendor-neutral, cloud-based solution that unifies device data and meets HIPAA standards, giving you clear visibility for managing cardiac monitoring.
Cyber risks will keep evolving, so staying prepared is key to handling challenges effectively while maintaining high-quality patient care. Don’t leave your RPM program exposed. Schedule a demo with RhythmScience to learn how Rhythm360 can support your practice with a secure foundation.